I was recently asked to facilitate an agile retrospective for another project here at SEP. After reviewing their project, I realized I didn't want to do one of the existing retro formats I knew of, because I was feeling like there was something missing from some of the standard ones (such as Sailboat). I decided to experiment with making my own. Thus was "The Project is a Highway" retro format born!
I was inspired by the fact that the project was related to roads and leaned into the metaphor. Take a moment to look at the drawing above (created by one of our talented UX folks).
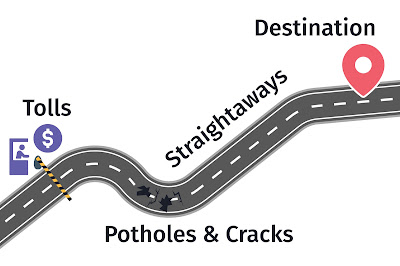
Here's each part of the model:
Tolls - These are prices you pay knowingly, usually to make the project better in the long run, or compromises that are required for business reasons (adding some tech debt to make a big milestone, using a certain technology to match the rest of the business, etc.) Are there any of these that might have been avoidable, possibly with different decisions in the past? Did any past decisions affect this work? There's nothing wrong with having some of these, but it's good to acknowledge why the project paid for them.
Straightaways - These are areas where the project went smoothly. What made them smooth, and can you get more of this in the future?
Potholes & Cracks - These are unexpected snags in the project, causing you to have a rough time, or to work around them and end up slowing down progress (unexpected end of life on a tool, for example).
The Destination - Did our destination change as we worked? Do we still have a vision of where the project is going? Do we all have the same vision? What comes next for the project that we should talk about?
After using this, I reflected on what, exactly, I liked about it over some other retrospective frameworks. One realization I had is that I like the Tolls metaphor specifically because it calls out that we sometimes make deliberate decisions to slow down feature work, which some other frameworks don't cover.